When Secrecy Becomes Mathematics: Turing and the Alchemy of Cryptography
R. Adams
10/2/2025
The instinct for patterns
Human beings have always lived by searching for patterns. We see figures in clouds, draw constellations in a chaotic sky, recognize faces in stains on a wall. That instinct saved our lives: spotting tracks in the soil meant prey or predator; noticing a shift in the wind could mean survival.
But the same impulse can betray us. When the pattern isn’t there, we invent it. And when someone builds a machine designed to erase it, our minds go blind.
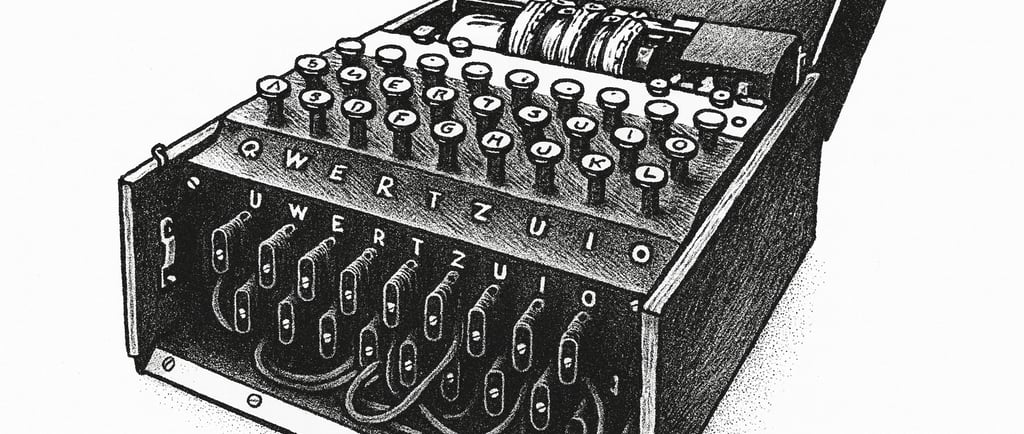
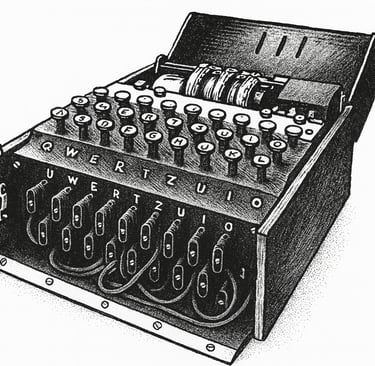
Enigma was precisely that: a device created to erase recognizable traces, to transform order into noise.
A code that seemed impossible
Imagine a typewriter where every key you press lights up a different letter on a panel of bulbs. You hit A, the light shows M. You press B, and you see Q. And not only that: inside the machine, wheels turn with every keystroke, reshuffling the alphabet all over again. The first A might be an M, the second an X, the third something else entirely.
That was the core of Enigma. Every day, the German army changed the positions of the wheels and the plugboard wiring, multiplying the possibilities to astronomical levels. The result: an encrypted message that, without the right setup, was nothing but gibberish.
How to think against chaos
The first idea at Bletchley Park was brute force: try every possible configuration. But the number was absurd: 10^114. To put it in perspective, the observable universe contains “only” about 10^80 atoms.
Alan Turing reframed the problem. Instead of asking how do I try everything?, he asked what can I discard without trying? That mental shift was the beginning of the breakthrough.
The first cracks in Enigma
Turing found hidden rules:
Enigma never encrypted a letter as itself. An A could never become A.
Many messages contained predictable fragments: greetings, weather reports, formulaic phrases (the famous cribs).
With those hints, there was no need to check the entire search space. It was enough to discard the impossible and shrink the problem to manageable proportions.
It was the move from brute force to logical reduction. From chaos to structure.
Mathematics behind the curtain
Each Enigma rotor was, in mathematical terms, a permutation: a function that reorders the alphabet. Several rotors chained together, plus the plugboard, produced a composition of functions that changed with every keystroke.
The number of combinations was immense, but the system was also full of constraints. And constraints are the cracks where logic slips in.
Turing realized that instead of searching for the needle in the haystack, you could burn the impossible straw. His machine, the Bombe, wasn’t just engineering: it was the physical embodiment of abstract thought. A mechanism to apply mathematics to noise.
From cryptography to universality
Once Enigma was defeated, a larger question remained. If a machine could follow rules to test hypotheses, why not generalize it? Why not imagine a machine capable of simulating any other process defined by rules?
Thus was born the universal Turing machine: a mental model of computation itself. Symbols, an infinite tape, and rules. Every modern computer, every program, every neural network descends from that intuition.
Philosophy of the invisible pattern
The depth of this story is not that Turing cracked a code, but how he thought while doing it. He showed that our obsession with seeing patterns isn’t enough when someone designs a system to hide them. At that point, we need abstraction: turning human instinct into mathematical logic, and logic into machine.
We still follow the same path today. Anomaly detection in AI or cybersecurity is not about watching everything at once, but about defining the impossible, the improbable, the suspicious. Just like Turing, we look for cracks in the noise.
Turing didn’t just defeat Enigma. He taught us that the true alchemy of cryptography lies at the intersection of the human mind and abstract mathematics. In realizing that secrecy is, in the end, always a hidden pattern.
R. Adams
Glossary
Enigma: Cipher machine used by the German army in World War II. Each keystroke lit up a different letter, and the system changed constantly thanks to its rotors.
Rotors: Internal wheels in Enigma that reordered the alphabet. Each keystroke made them rotate, changing the mapping between letters.
Plugboard: A panel of cables that swapped pairs of letters before and after the rotors, multiplying the number of possible configurations.
Cribs: Fragments of plaintext expected to appear in messages (such as greetings or weather reports). Used as clues to reduce possibilities.
Permutation: In mathematics, a reordering of elements. In Enigma, each rotor represented a permutation of the alphabet.
Composition of functions: When several operations are chained together. In Enigma, each rotor applied a permutation, and the result passed to the next.
Bombe: Machine built at Bletchley Park under Turing’s direction to test Enigma configurations and discard impossible ones at high speed.
Turing machine: Mathematical model proposed by Alan Turing. An abstract device that manipulates symbols on an infinite tape according to a finite set of rules. It is the foundation of the modern idea of the computer.
Cybersecurity & Architecture
Exploring the future of technology, security, and digital design.
Contact
© 2025. All rights reserved.
info@securitychronicles.tech
